Cybersecurity researchers have made light on a new Linux kernel exploitation technique called SLUBstickwhich could be exploited to elevate a limited heap vulnerability to an arbitrary memory read/write primitive.
SLUBStick, How the New Linux Kernel Hacking Technique Works
“Initially, it exploits an allocator timing side channel to perform a cross-cache attack reliably.“, said a group of academics from the Graz University of Technology (report visible via this PDF) and the experts then added: “Concretely, exploiting side-channel leakage brings the success rate above 99% for frequently used general-purpose caches..”
Memory security vulnerabilities that affect the Linux kernel have limited capabilities and are much more difficult to exploit due to security features such as supervisor mode access prevention (SMAP), kernel address space layout randomization (KASLR) and kernel control flow integrity (kCFI).
Fortunately, SLUBStick appears to have some limitations.
While software cross-cache attacks were devised as a way to counter kernel hardening strategies such as coarse heap splittingstudies have shown that existing methods have only a 40% success rate.
SLUBStick has been demonstrated on Linux kernel versions 5.19 and 6.2 using nine security vulnerabilities (e.g., double free, use after free, and out-of-bounds writing) discovered between 2021 and 2023, leading to unauthenticated root elevations and container escapes.
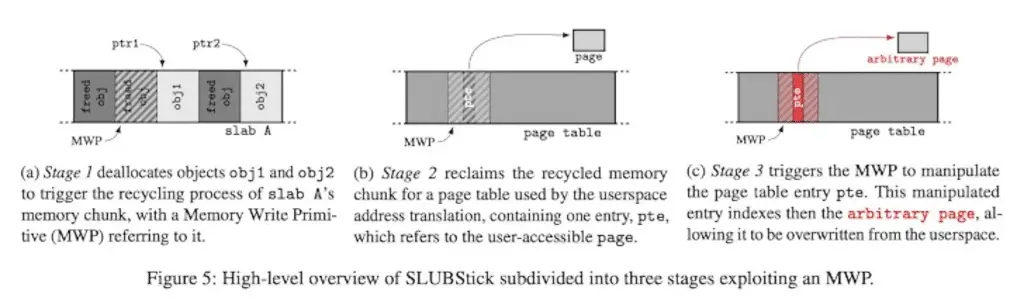
The main idea behind the approach is to provide the ability to modify kernel data and obtain arbitrary memory read and write primitives in a way that reliably bypasses existing defenses such as KASLR.
However, for this to work, the threat model assumes that there is a heap vulnerability in the Linux kernel and that an unprivileged user has code execution capabilities.
“SLUBStick exploits newer systems, including versions 5.19 and 6.2, for a wide range of heap vulnerabilities.“, the researchers said.
Linux, the myth of its “impenetrability” increasingly less true
Despite Linux’s reputation as a highly secure and nearly impenetrable operating system, Techniques like SLUBStick demonstrate that this perception is increasingly far from reality.
SLUBStick is not in fact the first method discovered to “perforate” the kernel: over the years, several advanced exploitation techniques have emerged that have highlighted previously unconsidered vulnerabilities.

One of the major security problems on Linux is the lack of a standardized method of virus detection, which makes it extremely difficult for users to know if their systems have been compromised and this little problem in security highlights the need for more robust solutions and greater awareness of emerging threats, especially in a context where attack techniques are becoming increasingly sophisticated.
If on Windows, for example, we have Windows Defender, there is no (currently) a counterpart on Linux operating systems, even if Open Source projects like ClamAV They come a little bit close (but are difficult to configure).
Recent vulnerabilities discovered on Linux
In recent times, several critical vulnerabilities have been discovered in the Linux kernel that highlight the need for greater attention to security. Some of these include:
- Dirty Pipe (CVE-2022-0847): a vulnerability that allows unprivileged users to overwrite data in read-only files.
- Spectre And Meltdown: families of vulnerabilities that exploit speculative processor execution to access sensitive data.
- StackRot (CVE-2023-3269): a vulnerability that allows escalation of privileges through improper stack management.
- BleedingTooth (CVE-2020-12351): a bug in the Bluetooth subsystem that allows remote execution of arbitrary code.
- Sequoia (CVE-2021-33909): a vulnerability that allows escalation of privileges by exploiting improper file system management.
These findings highlight that while Linux is generally considered secure, it is not immune to serious vulnerabilities that require timely attention and updates.
#SLUBStick #Linux #Kernel #Exploitation #Technique
