Cybersecurity researchers have discovery a new malicious package in the Python Package Index (PyPI) repository that masquerades as a library from the Solana blockchain platform, but which is actually designed to steal victims’ confidential information.
It is worth noting that in recent times, it is not uncommon for malicious packages created in Python to be used for malicious purposes.
Malicious Package Crafted in Python: Here’s What Researchers Know
“The legitimate Solana Python API project is known as ‘solana-py’ on GitHub, but simply ‘solana‘ in the Python software registry, PyPI“, has declared Sonatype researcher Ax Sharma in a report published last week, regarding this malicious package; the researcher then added that: “This slight discrepancy in names was exploited by a malicious actor who published a ‘solana-py’ project on PyPI.”
The malicious package “solana-py” attracted a total of 1,122 downloads since it was released on August 4, 2024. It is no longer available for download on PyPI.
The malicious package has additional python code compared to the original counterpart
The most surprising aspect of this malicious package’s library programmed in Python language is that it reported version numbers 0.34.3, 0.34.4 and 0.34.5; the latest version of the legitimate “solana” package is 0.34.3. This clearly indicates an attempt by the malicious actor to trick users searching for “solana” into inadvertently downloading “solana-py”.
Additionally, the malicious package copies the real code from its counterpart, but injects additional code into the “init.py” script which is responsible for collecting Solana blockchain wallet keys from the system.
This information is then exfiltrated to a domain of Hugging Face Spaces operated by the cyber criminal (“treeprime-gen.hf[.]space”), highlighting once again how various cyber criminals are abusing legitimate services for malicious purposes.
What are the risks of this malicious package created in Python language?
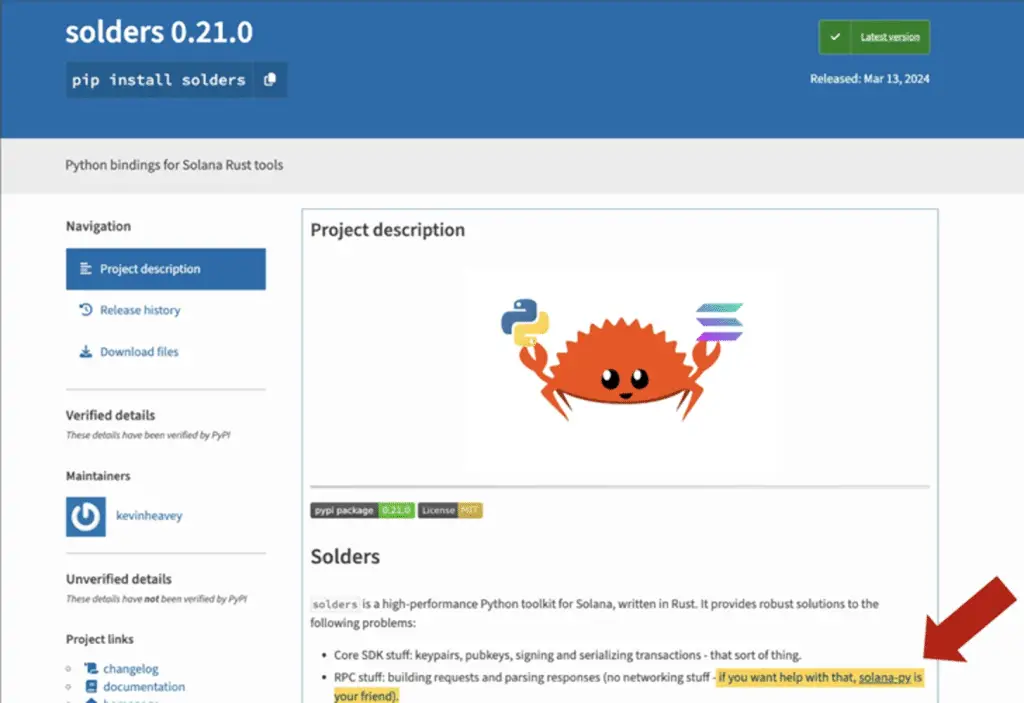
The attack campaign poses a supply chain risk, as Sonatype’s investigation found that legitimate libraries such as “solders” reference “solana-py” in their PyPI documentation, leading to a scenario where developers may have mistakenly downloaded “solana-py” from PyPI, thus expanding the attack surface.
“In other words, if a developer using the legitimate PyPI package ‘solders’ in their application is misled (by the solders documentation) into falling for the typographically-erroneous ‘solana-py’ project, would inadvertently introduce a cryptocurrency theft program into their application“, Sharma explained.
Cybersecurity researcher Sharma later stated that: “This would not only steal their secrets, but also those of any user running the developer’s application..”
The revelation comes as Phylum said it had identified hundreds of thousands of spam packets on npm containing Tea protocol abuse markers, a campaign that emerged over the first time in April 2024.
“The Tea Protocol project is taking steps to address this issue.“, the supply chain security firm said. “It would be unfair for legitimate Tea participants to have their compensation reduced because others are cheating the system. Additionally, npm has started removing some of these spammers, but the removal rate does not match the rate of new posts.“
The Double Face of Open Source
While it is true that Open Source allows you to solve problems practically in real time (provided you have prior knowledge of the programming language involved), on the other hand it is true that anyone (if expert in a certain language) having access to the code can create all sorts of imaginable computer damage.
Very often (reluctantly), we forget about this double face of Open Source and this case in which a malicious package created in Python is involved, reminds us of it.
#Malicious #Python #Package #Impersonates #Solana #Platform