Cybersecurity researchers have discovery a new variant of the Gafgyt botnet that targets machines with weak SSH passwords to mine cryptocurrencies on compromised instances using GPU computational power.
Gafgyt Botnet: Here’s How It Evolved According to Experts
This indicates that the “IoT botnet is targeting more robust servers operating in cloud-native environments“, has said Aqua Security researcher Assaf Morag in an analysis on Wednesday.
The Gafgyt botnet (also known as BASHLITE, Lizkebab and Torlus), active in the IT environment since at least 2014, has a history of exploitation weak or default credentials to take control of devices such as routers, cameras, and digital video recorders (DVRs); It is also capable of exploiting known security flaws in Dasan, Huawei, Realtek, SonicWall and Zyxel devices.
Infected devices are gathered into a botnet capable of launching Distributed Denial of Service (DDoS) attacks against targets of interest; there are evidence which suggest that the Gafgyt and Necro botnets are operated by a cybercriminal group called Keksec, also known as Kek Security and FreakOut.
IoT threats like the Gafgyt botnet are they evolve constantly to add new features, with variants detected in 2021 that They use the TOR network to hide malicious activityas well as borrowing some modules from the leaked Mirai source code. It is worth noting that Gafgyt’s source code has been Published online in early 2015, further fueling the emergence of new versions and adaptations.
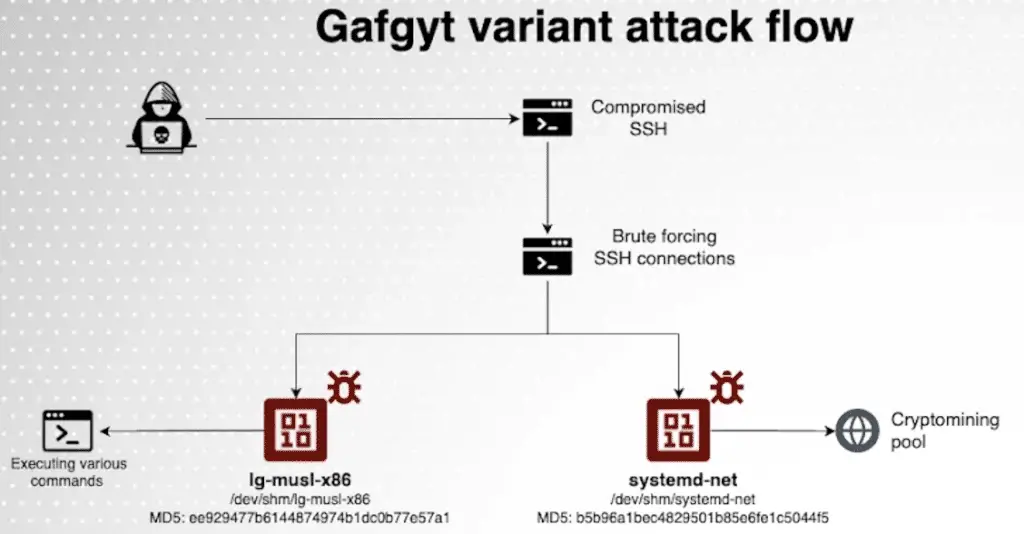
The latest attack chains involve brute-forcing SSH servers with weak passwords to deliver next-stage payloads and facilitate a cryptocurrency mining attack using “systemd-net”, but not before terminating any competing malware already running on the compromised host.
Gafgyt Botnet and Nvidia Graphics Cards
It also runs a worming module, a Go-based SSH scanner called ld-musl-x86, which is responsible for scanning the Internet for unsafe servers and propagating the malware to other systems, thus expanding the size of the botnet and this includes SSH, Telnet and credentials to game servers and cloud environments such as AWS, Azure, and Hadoop.
“The cryptominer used is XMRig, a Monero cryptocurrency miner“, said Morag. “However, in this case, the cyber criminal [o i criminali informatici] near [o cercano] to run a cryptominer using the –opencl and –cuda flags, that exploit the computational power of GPUs and Nvidia GPUs.”
Morag then added that “This, combined with the fact that the primary impact of the cybercriminal [o dei criminali informatici] It is crypto-mining rather than DDoS attacks, supports our claim that this variant differs from previous ones. It is aimed at targeting cloud native environments with strong CPU and GPU capabilities.”
Data collected by querying Shodan shows that there are over 30 million publicly accessible SSH servers, making it essential that users take steps to secure instances against brute-force attacks and potential exploits.
Similar cases occurred in the past
The case of the Gafgyt botnet is certainly not the only one of its kind and in the past, several similar cases of IoT botnets exploiting security vulnerabilities for malicious purposes have been observed.
Some examples include I will seewhich in 2016 exploited IoT devices with default credentials to launch massive DDoS attacks; Hajimea malware that spread similarly to Mirai but sought to protect infected devices from other threats; and Reaperwhich expanded the range of compromised devices using as-yet-unpatched vulnerabilities rather than just weak credentials.
These cases demonstrate the constant evolution of IoT threats and the need to strengthen the security of networked devices.
#Gafgyt #Botnet #Variant #Targets #Cryptocurrency #Miners
