Cybersecurity researchers have shed light on a sophisticated information theft campaign that mimics legitimate brands to distribute malware such as DanaBot And StealC.
DanaBot and StealC: Where Do These Malwares Come From and What Do They Do?
The cluster of activities, orchestrated by Russian-speaking cybercriminals and collectively codenamed Tusk, is said to comprise several sub-campaigns, exploiting the platforms’ reputations to trick users into downloading the malware via fake websites and social media accounts.
“All active sub-campaigns host the initial downloader on Dropbox“, they have affirmed Kaspersky researchers Elsayed Elrefaei and AbdulRhman Alfaifi. “This downloader is responsible for delivering additional malware samples to the victim’s machine, which are mostly info-stealers (DanaBot and StealC) and clippers..”
The identified sub-campaigns all belong to a single
Of the 19 sub-campaigns identified to date, three are currently active; the name “Tusk” is a reference to the threat word “Mammoth” used by cybercriminals in log messages associated with the initial downloader, however it is worth noting that mammoth is a slang term often used by Russian cybercrime groups to refer to victims.
The campaigns are also notable for using phishing tactics to trick victims into sharing their personal and financial information, which is then sold on the dark web or used to gain unauthorized access to their gaming accounts and cryptocurrency wallets.
The first of three sub-campaigns, known as TidyMe, mimics peerme[.]I have a similar site hosted on tidyme[.]me (in addition to tidymeapp[.]me and tidyme[.]app) that asks for a click to download a malicious program for Windows and macOS systems, distributed via Dropbox.
The downloader is an Electron application that, when launched, asks the victim to enter the displayed CAPTCHA, after which the application’s main interface is shown, while two additional malicious files are secretly retrieved and executed in the background.
Both payloads observed in the campaign are artifacts of Hijack Loaderwhich eventually launch a variant of the StealC malware with the ability to gather a wide range of information.
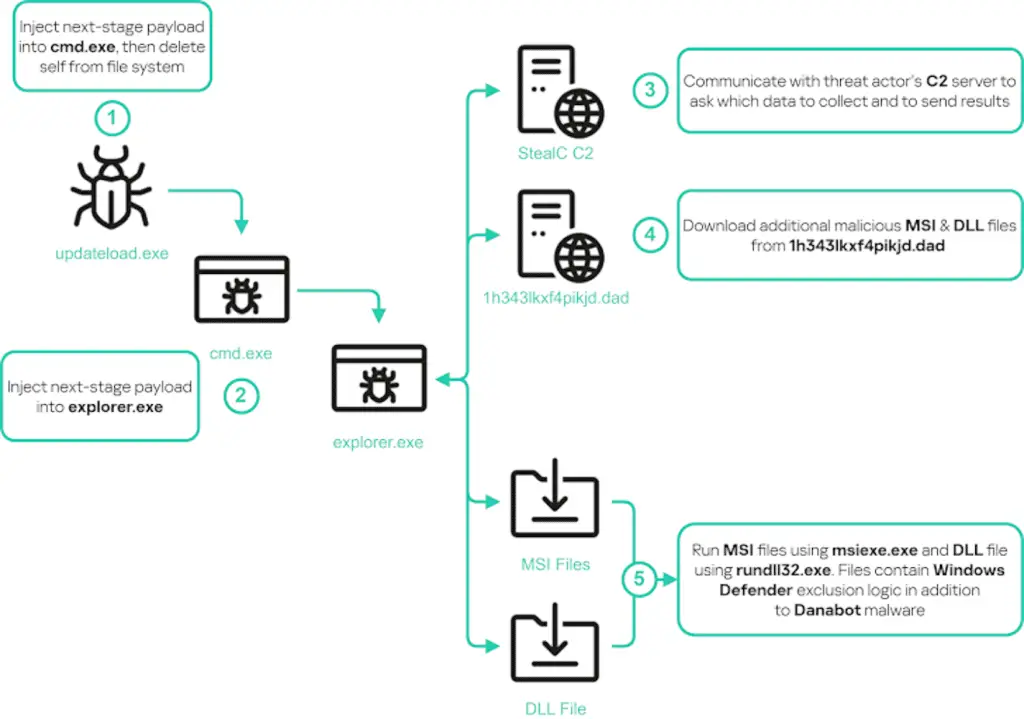
The Importance of the Second Sub-Campaign of the Tusk Campaign
RuneOnlineWorld (“runeonlineworld[.]io”), the second sub-campaign, involves the use of a fake website simulating a massively multiplayer online game (MMO) called Rise Online World to distribute a lookalike downloader that opens the door for DanaBot and StealC to be installed on compromised systems.
Also distributed via Hijack Loader in this campaign is a Go-based clipper malware, designed to monitor the contents of the clipboard and replace wallet addresses copied by the victim with a Bitcoin wallet. controlled by the attacker to perform fraudulent transactions.
Rounding out the active campaigns is Voico, which mimics an AI translation project called YOUS (yous[.]ai) with a malicious counterpart called voico[.]I to spread an initial downloader that, upon installation, asks the victim to fill out a registration form with their credentials, then recording the information on the console.

The final payloads show similar behavior to the second sub-campaign, with the only difference being that the StealC malware used in this case communicates with a different command and control (C2) server.
“The campaigns […] demonstrate the persistent and evolving threat posed by cybercriminals who are adept at mimicking legitimate designs to deceive victims,” the researchers said. “The reliance on social engineering techniques such as phishing, combined with multi-stage malware delivery mechanisms, highlights the advanced capabilities of the various cybercriminals involved..”
Cybersecurity researchers finally concluded that “By leveraging the trust that users place in well-known platforms, These attackers effectively distribute a range of malware designed to steal sensitive information, compromise systems, andultimately, obtain financial gains.“
#DanaBot #StealC #Malware #Campaign #Coming #Russia