Cybersecurity researchers have discovery several critical flaws in the services offered by Amazon Web Services (AWS) that, if successfully exploited, could lead to serious consequences.
What are the problems encountered in Amazon Web Services (AWS)
“The impact of these vulnerabilities ranges from remote code execution (RCE), to full user account control (which could provide powerful administrative access), to manipulation of artificial intelligence modules, sensitive data exposure, data exfiltration and denial-of-service“, has declared Cloud security firm Aqua in a detailed report.
After a responsible reporting in February 2024, Amazon addressed the deficiencies over several months, from March to June and the results were introduce yourself at Black Hat USA 2024.
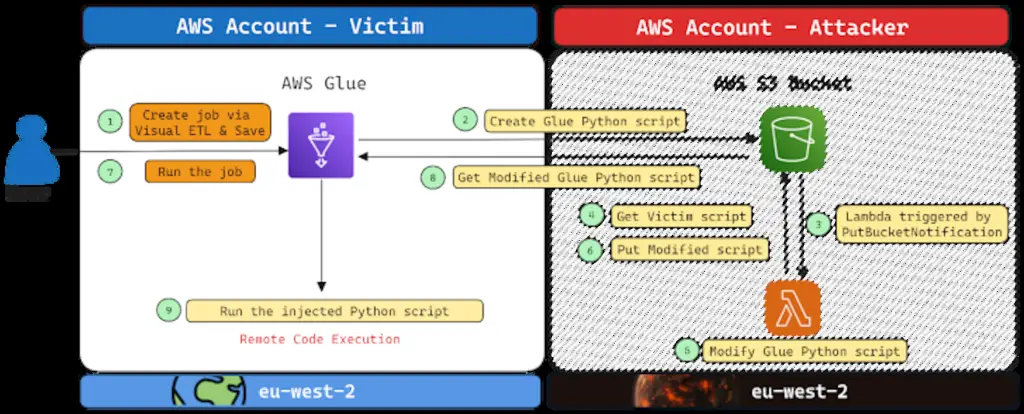
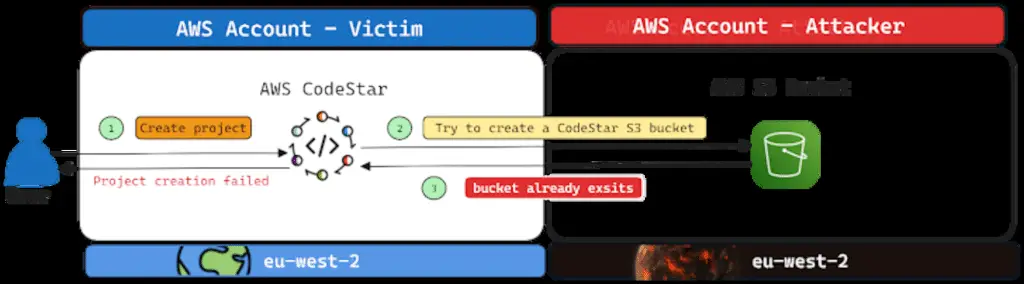
At the heart of the problem, dubbed Bucket Monopoly, is an attack vector called Shadow Resource, which in this case refers to the automatic creation of an Amazon Web Services S3 bucket when using services like CloudFormation, GlueEMR, SageMaker, ServiceCatalog e CodeStar.
The name of the S3 bucket created in this way is unique and follows a default naming convention (for example, “cf-templates-{Hash}-{Region}”); an attacker could exploit this behavior to configure buckets in Amazon Web Services regions do not use and wait for a client of this legitimate service to use one of the vulnerable services to gain covert access to the contents of the S3 bucket.
Based on the permissions granted to the adversary-controlled S3 bucket, this approach could be used to trigger a DoS condition, execute code, manipulate or steal data, and even gain full control of the victim’s account without the user’s knowledge.
The Problems Bucket Monoply Causes on Amazon Services
To maximize the chances of success, using Bucket Monopoly, attackers can create unclaimed buckets in all available regions in advance and store malicious code in the bucket, and when the target organization first enables one of the vulnerable services in a new region, the malicious code will be executed unknowingly, cwith the potential creation of an admin user that can grant control to attackers.
However, it is important to note that the attacker will have to wait for the victim to deploy a new CloudFormation stack in a new region for the first time to successfully launch the attack. Modifying the CloudFormation template file in the S3 bucket to create a rogue admin user also depends on whether the victim’s account has permissions to manage IAM roles.
Aqua said it found five other AWS services that rely on a similar naming methodology for S3 buckets – {Service Prefix}-{AWS Account ID}-{Region} – thus exposing them to Shadow Resource attacks and ultimately allowing a malicious cybercriminal to perform malicious actions, including denial of service, information disclosure, data manipulation, and arbitrary code execution:
- AWS Glue: aws-glue-assets-{Account-ID}-{Region}
- AWS Elastic MapReduce (EMR): aws-emr-studio-{Account-ID}-{Region}
- AWS SageMaker: sagemaker-{Region}-{Account-ID}
- AWS CodeStar: aws-codestar-{Region}-{Account-ID}
- AWS Service Catalog: cf-templates-{Hash}-{Region}
Amazon’s Statements
The company also has observed that AWS account IDs should be considered confidential, contrary to what Amazon states in its documentation, as they could be used to orchestrate similar attacks.
Additionally, hashes used for AWS accounts can be discovered using regular expression searches on GitHub or Sourcegraphor alternatively, by examining open issues, thus making it possible to reconstruct the S3 bucket name even in the absence of a way to calculate the hash directly from the account ID or other account-related metadata.
“This attack vector affects not only AWS services, but also many open-source projects used by organizations to deploy resources in their AWS environments.“, Aqua said. “Many open-source projects automatically create S3 buckets as part of their functionality or instruct their users to deploy S3 buckets.“
“Instead of using predictable or static identifiers in the bucket name, we recommend generating a unique hash or random identifier for each region and account, and embedding this value in the S3 bucket name. This approach helps protect against attacks where buckets are prematurely claimed by attackers..”
#AWS #Vulnerabilities #Amazon #Services