Cybersecurity researchers have discovery vulnerabilities in Sonos smart speakers that could be exploited by cybercriminals to secretly listen in on users.
What are the vulnerabilities of Sonos speakers?
The vulnerabilities “led to a complete breach in the security of Sonos’ secure boot process across a wide range of devices and the ability to compromise multiple devices remotely via an over-the-air attack“, they have declared NCC Group security researchers Alex Plaskett and Robert Herrera.
Successful exploitation of one of these flaws could allow a remote attacker to obtain a secret audio capture from Sonos devices via an over-the-air attack and they concern all previous versions to the Sonos S2 release 15.9 and Sonos S1 release 11.12, which were released in October and November 2023, respectively.
The findings were presented at Black Hat USA 2024. A description of the two security flaws is as follows:
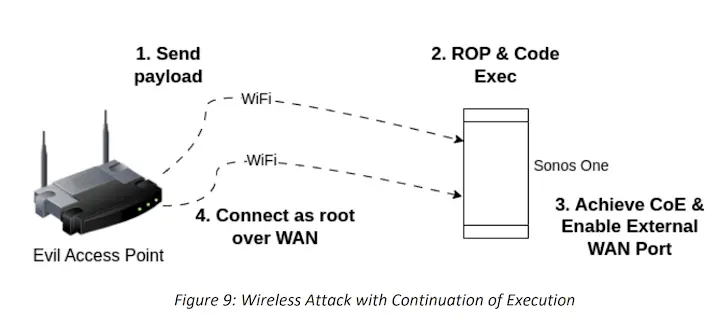
- CVE-2023-50809: A vulnerability in the Sonos One Gen 2 Wi-Fi stack does not properly validate an information element during the negotiation of a WPA2 four-way handshake, leading to remote code execution.
- CVE-2023-50810: A vulnerability in the U-Boot component of the Sonos Era-100 firmware that could allow persistent execution of arbitrary code with Linux kernel privileges.
Driver Issues According to MediaTek
The NCC Group, which reverse-engineered the boot process to achieve remote code execution on the Sonos Era-100 and Sonos One devices, said that CVE-2023-50809 is the result of a memory corruption vulnerability in the wireless driver of the Sonos One, which is a third-party chipset manufactured by MediaTek.
“In the wlan driver, there is a possible out-of-bounds write due to incorrect input validation“, has declared MediaTek in an advisory for CVE-2024-20018. “This could lead to local privilege escalation without the need for additional execution privileges. No user interaction is required for exploitation..”
The initial access gained in this way paves the way for a series of post-exploitation steps that include gaining a full shell on the device to gain complete control of the smart speaker in the root context, followed by the deployment of a new Rust rig capable of capturing audio from the microphone within a short physical distance of the speaker.
There is also a flaw in the boot process
The other flaw, CVE-2023-50810, involves a chain of vulnerabilities identified in the secure boot process to exploit Era-100 devices, effectively making it possible to bypass security checks to allow the execution of unsigned code in the context of the kernel.
This could then be combined with an N-day privilege escalation flaw to facilitate code execution at the ARM EL3 and extract hardware-backed cryptographic secrets.
“Overall, there are two important conclusions to draw from this research.“, the researchers said. “The first is that OEM components must be of the same security standard as in-house components. Vendors should also perform threat modeling of all external attack surfaces of their products and ensure that all remote vectors have undergone sufficient validation..”
“In the case of secure boot weaknesses, it is important to validate and test the boot chain to ensure that these weaknesses are not introduced. Both hardware and software-based attack vectors should be considered..”
The disclosure comes as firmware security firm Binarly revealed that hundreds of UEFI products of nearly a dozen vendors are susceptible to a critical firmware supply chain issue known as PKfail, which allows attackers to bypass Secure Boot and install malware.
In particular, it found that hundreds of products use a test platform key generated by American Megatrends International (AMI), which was likely included in their reference implementation in the hope that it would be replaced with another key securely generated by entities further down the supply chain.
The most affected hardware
“The problem arises from the Secure Boot ‘master key’, known as the Platform Key (PK) in UEFI terminology, which is untrusted because it is generated by the Independent BIOS Vendors (IBV) and shared between different vendors.,” he said, describing it as a cross-platform issue affecting both x86 and ARM architectures.

“This platform key […] is often not replaced by device manufacturers or OEMs, resulting in devices that ship with untrusted keys. An attacker with access to the private part of the PK can easily bypass Secure Boot by manipulating the Key Exchange Key (KEK) database, the signature database (db), and the forbidden signature database (dbx).”
As a result, PKfail allows cybercriminals to execute arbitrary code during the boot process, even with Secure Boot enabled, allowing them to sign malicious code and distribute a UEFI bootkit, such as BlackLotus.
“The first firmware vulnerable to PKfail was released in May 2012, while the last one was released in June 2024.“, Binarly said. “Overall, this makes this supply chain issue one of the longest-running of its kind, lasting more than 12 years.“
#Sonos #Smart #Speaker #Flaw #Discovered