An analysis of the Malware logs for the theft of information published on the dark web led to the discovery of thousands of consumers of child pornography (CSAM), indicating how such information could be used to combat serious crime.
How CSAM Users Were Caught
“Approximately 3,300 unique users were found with accounts on known CSAM sources“, has declared Recorded Future in a proof-of-concept (PoC) report released last week. “A notable 4.2% had credentials from multiple sources, suggesting a greater likelihood of criminal behavior.“
In recent years, variants of info–stealer (literally personal information stealing programs) ready to use have become a threat pervasive And ubiquitous affecting various operating systems with the aim of stealing sensitive information such as credentials, cryptocurrency wallets, payment card data and screenshots.
This is evidenced by the rise of new stealer malware variants such as Kematian Stealer, Neptune Stealer, 0bj3ctivity, Poseidon (formerly known as RodStealer), Satan Stealer And StrelaStealer.
How these malware were distributed
Distributed via phishing, spam campaigns, cracked software, fake update websites, SEO poisoning and malvertising, the data collected using such programs typically finds its way onto the dark web in the form of stealer logswhere they are purchased by other cyber criminals to further their schemes.
“Employees regularly save corporate credentials on personal devices or access personal resources on organizational devices, increasing the risk of infection“, has noticed Flare in a report last July and then added: “There is a complex ecosystem where malware-as-a-service (MaaS) vendors sell info-stealer malware on illicit Telegram channels, cybercriminals distribute through fake cracked software or phishing emails, and then sell the logs of infected devices on specialized dark web marketplaces.“
How many users have been caught browsing these controversial sites?
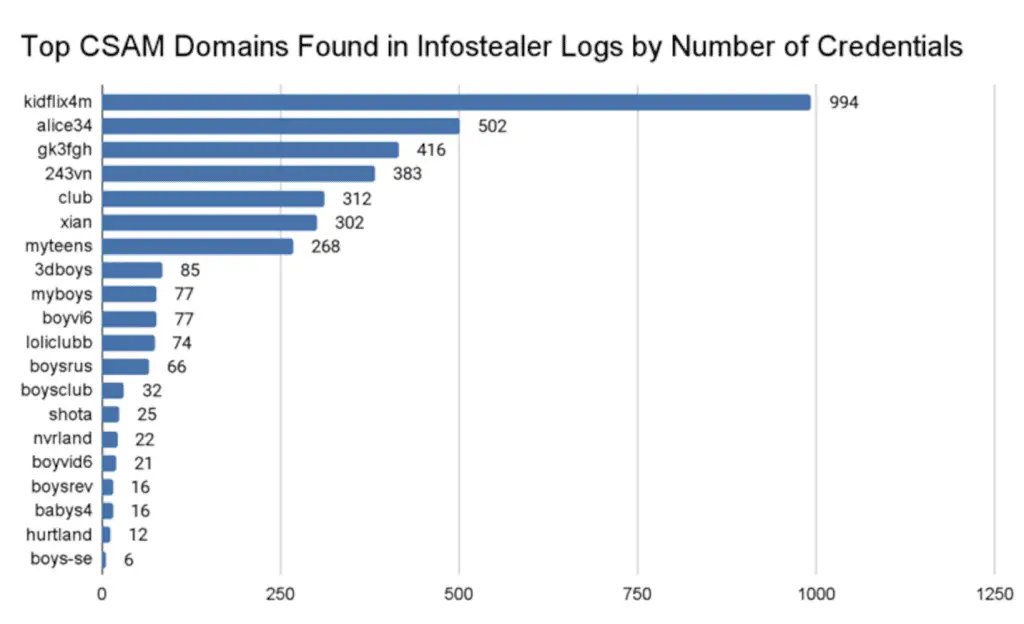
Recorded Future’s Insikt group has stated of being able to identify 3,324 unique credentials used to access known CSAM domains between February 2021 and February 2024using them to expose three individuals who were found to maintain accounts on no fewer than four websites.

The fact that the stealer logs also include cryptocurrency wallet addresses means that could be used to determine whether the addresses were used to procure CSAM and other malicious material.
From which countries were the users involved in these sites present on the dark web?
Additionally, countries like Brazil, India, and the United States had the highest numbers of users with credentials for known CSAM communities, although the company said that this could be due to a “overrepresentation due to the origin of the dataset.”
“Info-stealer malware and stolen credentials are set to remain a mainstay of the cybercriminal economy due to high demand from threat actors seeking initial access to targets.“, cybersecurity experts said, adding that he had shared his findings with law enforcement.

“Info-stealer logs can be used by investigators and law enforcement partners to track child exploitation [CSAM] on the dark web and provide insight into a particularly difficult-to-trace part of the dark web.”
Similar CSAM cases occurred in the past
In recent years, several similar cases have emerged involving the use of information-stealing malware to detect and combat illegal activities, including sexual exploitation of minors (so CSAM cases). Here are some examples:
- Operation Pacifier (2015-2017): The FBI conducted an operation against the child pornography website “Playpen”; using an exploit in the Tor software, the FBI was able to take control of the website’s server and collect information about users. This operation led to hundreds of arrests worldwide and the identification of many victims..
- Freedom Hosting Case (2013): Freedom Hosting, one of the largest dark web hosting providers, has been infiltrated by the FBI; using a JavaScript exploit, the FBI was able to collect information about users accessing sites hosted on Freedom Hosting, many of which contained child pornography. This led to the arrest of the Freedom Hosting operator and the shutdown of numerous illegal sites..
- Darknet Child Pornography Bust (2018): German authorities, in collaboration with other countries, have dismantled one of the largest child pornography platforms on the dark web, “Elysium,” resulting in the arrest of several members and the discovery of hundreds of victims. The investigations used advanced cyber intelligence techniques to track and identify users of the site.
- Welcome to Video Case (2019): Law enforcement agencies in several countries, including the United States, the United Kingdom and South Korea, have taken down the site “Welcome to Video,” one of the largest bitcoin-based child pornography platforms, resulting in the arrest of hundreds of people and the release of several victims. The use of bitcoin transactions allowed investigators to trace payments and identify users of the site.
These cases demonstrate how law enforcement is increasingly using advanced technologies and international collaboration to fight dark web crime and protect victims of sexual exploitation.
#CSAM #Malware #Reveals #Accounts #Controversial #Sites