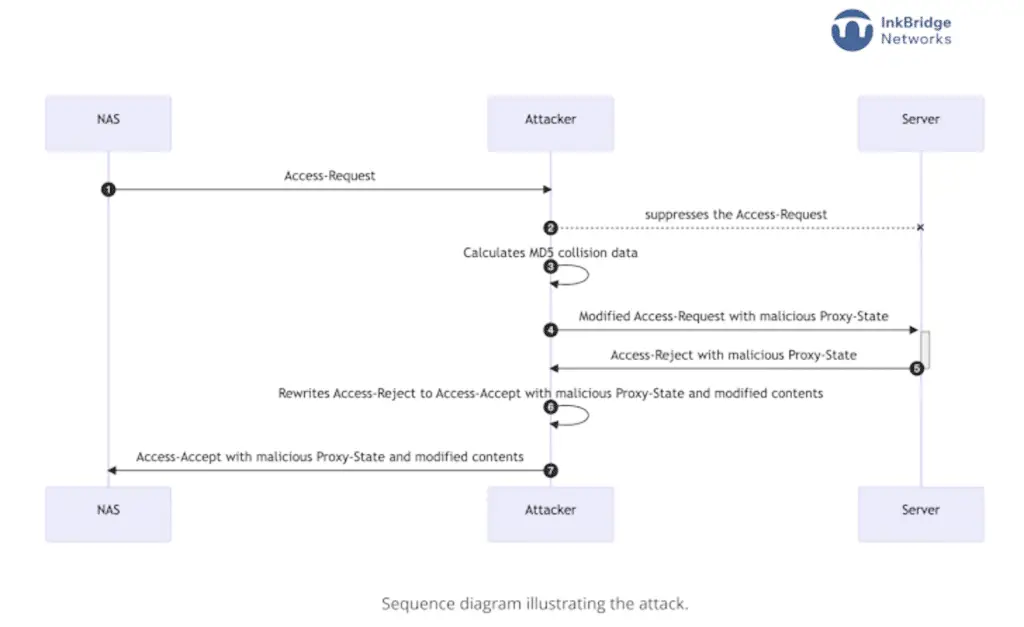
Cybersecurity researchers have discovery a vulnerability in the network authentication protocol called RADIUS call BlastRADIUS, which could be exploited by an attacker to perform Mallory-in-the-middle (MitM) attacks and bypass integrity checks under certain circumstances.
All the problems related to the RADIUS protocol according to cybersecurity researchers
“The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks.“, said Alan DeKok, CEO of InkBridge Networks and creator of the project, in a statement FreeRADIUSwho later added: “As a result, an attacker can modify these packets without being detected. The attacker would be able to force any user to authenticate and grant any permission (VLAN, etc.) to that user..“
The RADIUS protocol, to put it very briefly, is nothing more than the acronym for Remote Authentication Dial-In User Serviceis a protocol client/server that provides centralized management of authentication, authorization, and accounting (AAA) for users connecting to and using a network service.
The security of the RADIUS protocol is based on a hash derived from the algorithm MD5considered cryptographically vulnerable starting from December 2008 due to the risk of collision attacks.
This means that Access-Request packets can be subject to what is called a chosen-prefix attack, which makes it possible to modify the response packet so that it passes all the integrity checks of the original response.
However, for the attack to be successful, the adversary must be able to modify the RADIUS packets in transit between the client and the server with the RADIUSM protocol enabled; therefore this also means that organizations sending packets over the Internet are at risk of vulnerabilities.
Other mitigating factors that prevent the power of the attack come from the use of TLS to transmit RADIUS traffic over the Internet. and by increasing the security of packages through the attribute Message Authenticator.
ISPs also need to be very careful about the BlastRADIUS vulnerability
BlastRADIUS is the result of a fundamental design flaw and is said to impact all standards-compliant RADIUS clients and servers, making it imperative that Internet Service Providers (ISPs) and organizations using the protocol upgrade to the latest version.
“In particular, the PAP, CHAP and MS-CHAPv2 authentication methods are the most vulnerable.“, DeKok said. “ISPs will need to update their RADIUS servers and network equipment.”
Dedok later added that “Anyone using MAC address or RADIUS authentication for administrator logins to switches is vulnerable. Using TLS or IPSec prevents the attack, and 802.1X (EAP) is not vulnerable..”
For enterprises, the attacker should already have access to the management VLAN (virtual local area network); additionally, ISPs may be susceptible if they send RADIUS traffic over intermediate networks, such as third-party outsourcers or the wider Internet. wide.
It is worth noting that the vulnerability, which has a CVSS score of 9.0, It particularly affects networks that send RADIUS/UDP traffic over the Internetgiven that “Most RADIUS traffic is sent ‘in the clear’.“
Have there been any actual attacks via BlastRADIUS? It would appear not.
Although the vulnerability is a verified fact, fortunately There is no evidence that it is actively exploited or that it has been exploited in relatively recent times.
“This attack is the result of the long-neglected security of the RADIUS protocol.“, said DeKok, who finally concluded by saying: “Although standards have long suggested protections that would prevent the attack, such protections have not been mandated. Furthermore, many vendors have not even implemented the suggested protections..”
#RADIUS #Protocol #Protocol #Exposed #MiTM #Vulnerabilities