Cybercriminals linked to North Korea have been observed by cybersecurity researchers while using poisoned Python packages as a means to distribute a new malware called PondRAT, as part of an ongoing campaign.
PondRAT, its discovery and its functioning
According to new findings from Palo Alto Networks Unit 42, PondRAT is considered a lighter version of POOLRAT (also known as SIMPLESEA), a backdoor for macOS already attributed to the Lazarus Group and used in attacks related to the 3CX supply chain compromise that occurred onlast year.
Some of these attacks are part of a persistent cyber attack campaign called Operation DreamJobwhere potential targets are lured with enticing job offers in an attempt to trick them into downloading malware.
“The attackers behind this campaign uploaded several poisoned Python packages to PyPI, a popular open-source Python package repository.“, said Yoav Zemah, researcher at Unit 42, linking the activity with moderate certainty to a cybercriminal group called Gleaming Pisces.
The adversary is also known to the cybersecurity community as Citrine Sleet, Labyrinth Chollima, Nickel Academy, and UNC4736, a subgroup of the Lazarus Group also known for distributing the AppleJeus malware.
The ultimate goal of the attacks is believed to be “to secure access to supply chain vendors through developer end points and subsequently gain access to vendor customer end points, as observed in previous incidents.”
The malicious Python packages used by PondRAT
The list of malicious packages, now removed from the PyPI repository, is as follows:
The infection chain is quite simple: the packages, once downloaded and installed on the developers’ systems, are designed to execute a coded next stage that, in turn, runs the Linux and macOS versions of the RAT malware after retrieving them from a remote server.
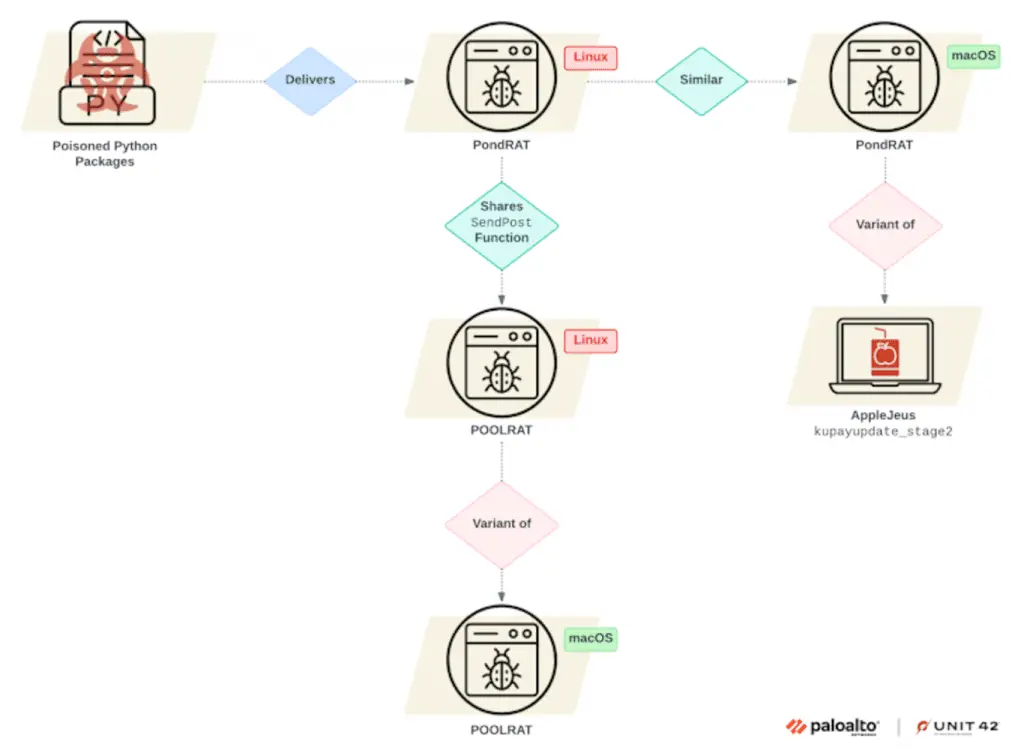
Further analysis of PondRAT revealed similarities to both POOLRAT and AppleJeus, with the attacks also distributing new Linux variants of POOLRAT.
“The Linux and macOS versions of POOLRAT use an identical functional structure to load their configurations, featuring similar method names and functionality.“, Zemah said, adding: “Furthermore, the method names in both variants are surprisingly similar, and the strings are nearly identical. Finally, the mechanism that handles commands from the command and control server is almost identical.”
PondRAT attacks not only macOS but also Linux
PondRAT, a leaner version of POOLRAT, has capabilities such as uploading and downloading files, suspending operations for a predefined period of time, and executing arbitrary commands.
“Testing of additional Linux variants of POOLRAT showed that Gleaming Pisces has improved its capabilities on both Linux and macOS platforms.,” said Unit 42, who then added: “Weaponizing legitimate-looking Python packages across multiple operating systems poses a significant risk to organizations. Successful installation of malicious third-party packages can lead to malware infections that compromise the entire network.“
The disclosure comes as KnowBe4, which was tricked into hiring a North Korean threat actor as an employee, has reported that more than a dozen companies “they hired North Korean employees or They have been besieged by a multitude of fake resumes and applications sent by North Koreans hoping to get a job in their organization..”
He described the activity, which CrowdStrike monitored under the name Famous Chollima, as an operation “complex, industrial, large-scale, nation-state” and said it represents a “serious risk for any company with employees who work only remotely.”
And what do you think about this latest malware created by North Korean attackers? Write it in the comments!

#PondRAT #Python #Malware #Attacks #Developers
