An earlier flexible “backdoor” named Kapeka has been “sporadically” observed, while being exploited in cyberattacks targeting Eastern Europe, including Estonia and Ukraine, at least from the beginning of 2022.
The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group known as Sandworm (also known as APT44 or as Seashell Blizzard); however Microsoft is tracking the same malware under the name KnuckleTouch.
What is known about Kapeka
“The malware […] is a flexible backdoor with all the features needed to serve as a starter kit for operators and also to provide long-term access to the victim's environment” has said security researcher Mohammad Kazem Hassan Nejad.
Kapeka comes with a “dropper” that is designed to launch and run a backdoor component on the infected host, after which it removes itself; The “dropper” it is also responsible for configuring backdoor persistence, both as a scheduled task and as an autorun logdepending on whether the process has system privileges (long story short: administrator privileges).
Microsoft's fight to eliminate the backdoor called Kapeka
Microsoft, in his notice published in February 2024, described Kapeka as being involved in multiple ransomware distribution campaigns and that it can be used to perform a variety of functions, such as stealing credentials and other data, conduct destructive attacks and give threat actors remote access to the device.
The backdoor in question is a Windows DLL written in C++ and features an integrated configuration of command and control (C2) used to establish contact with a server controlled by a remote hacker and contains information about how often you need to query the server to retrieve commands.
As well as masquerading as a add-on of Microsoft Word to make it authentic at least in appearance, the backdoor DLL collects information about the compromised host and implements multithreading to recover incoming instructionsprocess them and exfiltrate the execution results to the C2 server.
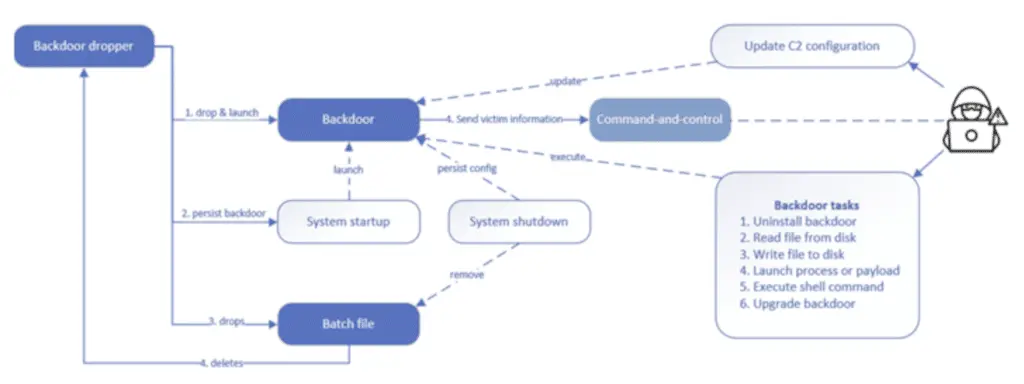
“The backdoor uses the WinHttp 5.1 COM interface (winhttpcom.dll) to implement its network communication component“, Nejad explained. “The backdoor communicates with its C2 to query tasks and send task information and results. The backdoor uses JSON to send and receive information from its C2.”
The system is also able to update its C2 configuration “on-the-fly” by receiving a new version from the C2 server while querying the data; some of the main features of the backdoor allow you to read and write files to and from disklaunch payloads, execute shell commands, and even update and uninstall.
What was the propagation method of this cyber threat?
The exact method through which the malware is propagated is currently unknown; However, Microsoft noted that the “dropper” is recovered from compromised websites using the certutil utility, highlighting the use of a legitimate binary (“living-off-the-land binary” or LOLBin) to orchestrate the attack.
Kapeka connections to Sandworm have conceptual and configuration overlaps with families previously disclosed as GreyEnergy, a likely successor to the BlackEnergy toolkit, and Prestige.

“Kapeka is likely to have been used in intrusions that led to the distribution of the Prestige ransomware in late 2022” said WithSecure. “Kapeka is likely to be the successor to GreyEnergywhich itself was likely a replacement for BlackEnergy in Sandworm's arsenal.“
In the end the company concluded by saying that “lhe victimology of backdoors, the infrequent sightings and the level of stealth and sophistication indicate APT-level activitymost likely of Russian origin.“
#Kapeka #backdoor #Russian #hackers