Microsoft is calling attention to a group of cybercriminals based in Moroccoknown as Storm-0539, responsible for gift card fraud and theft through highly sophisticated email and SMS phishing attacks.
How virtual gift card fraud works
“Their main goal is to steal gift cards and profit from them by selling them online at a discounted price“, has stated the company in its latest Cyber Signals report. “We have seen some examples where the group of cyber criminals stole up to $100,000 a day from some businesses“.
Storm-0539 was highlighted first by Microsoft in mid-December 2023, linking it to social engineering campaigns ahead of the year-end holidays to steal victims’ credentials and session tokens via adversary-in-the-middle (AitM) phishing pages.
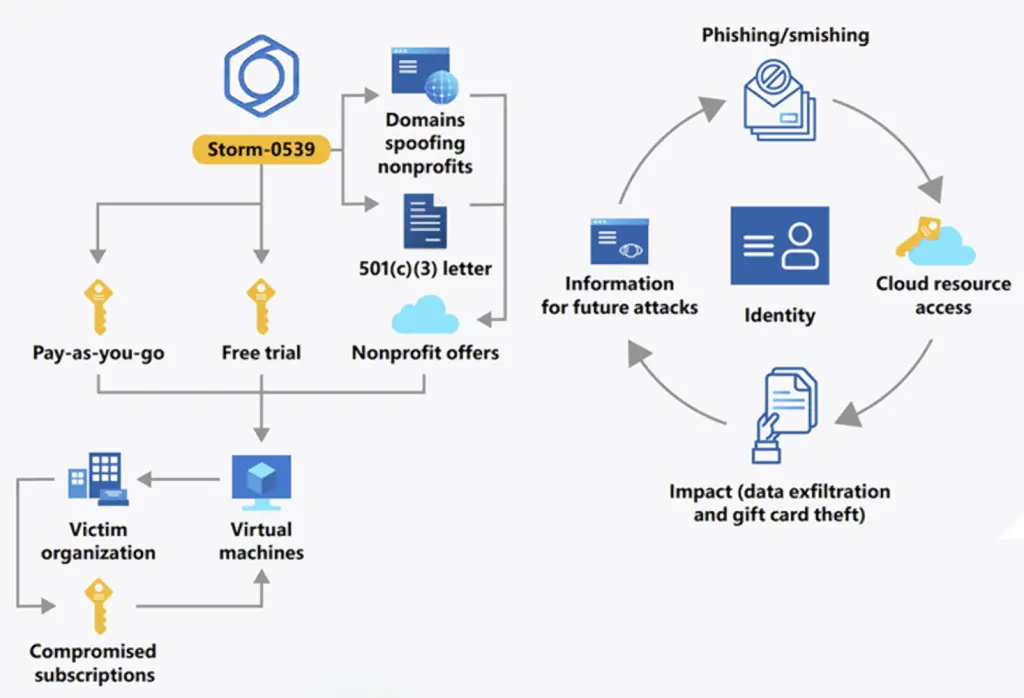
The group, also known as Atlas Lion and active since at least the end of 2021, is known to abuse initial access by enrolling their devices to bypass authentication and gain persistent accessgain elevated privileges, and compromise gift card services by creating fake gift cards to facilitate fraud.
How attack chains were organized with virtual gift cards
The attack chains are further designed to gain covert access to the victim’s cloud environment, allowing the cybercriminal group to perform extensive reconnaissance and exploit the infrastructure to achieve their ultimate objectives; Campaign targets include large retailers, luxury brands and popular fast-food restaurants.
The ultimate goal of the operation is to redeem the value associated with these cards, sell the gift cards to other cybercriminals on black markets, or use “money mules” to cash in on the gift cards.
Criminal targeting of gift card portals marks a tactical evolution for the hacker group, which previously engaged in stealing payment card data using malware on point-of-sale devices (PoS).
The Windows maker said it observed a 30% increase in Storm-0539 intrusion activity between March and May 2024, portraying attackers as exploiting their deep knowledge of the cloud For “Conduct reconnaissance of an organization’s gift card issuing processes“.
Earlier this month, the US Federal Bureau of Investigation (FBI) released a notice in PDF warning of smishing attacks perpetrated by the group that target the gift card departments of retail corporations using a sophisticated phishing kit to bypass multi-factor authentication (MFA).
“In one case, a corporation detected fraudulent Storm-0539 gift card activity in their system and has instituted changes to prevent the creation of fraudulent gift cards“, the FBI said.
“Those behind the group [hacker marocchino] Storm-0539 continued their smishing attacks and regained access to company systems. Then, the perpetrators changed tactics to locate the unredeemed gift cards and changed the email addresses associated with those controlled by the Storm-0539 cybercriminals to redeem the gift cards.”
Phishing yes, but not just credential theft
It is worth noting that cybercriminals’ activities go beyond stealing login credentials of gift card department staff, their efforts also extend to acquiring passwords and secure shell (SSH) keys, which could then be sold for financial gain or used for subsequent attacks.
Another tactic employed by Storm-0539 involves using legitimate internal mailing lists to spread phishing messages once initial access is gained, adding a veneer of authenticity to the attacks. It has also been found to create free trials or student accounts on cloud service platforms to set up new websites.
Abuse of cloud infrastructure, including impersonating legitimate nonprofits at cloud providers, is a sign that financially motivated groups are taking cues from the playbooks of advanced state-sponsored perpetrators to disguise their operations and remain undetected .
The word to Microsoft
Microsoft is urging gift card companies to treat their gift card portals as high-value targets by monitoring suspicious logins.
“Organizations should also consider integrating MFA with conditional access policies where authentication requests are evaluated using additional identity signals such as IP address location information or device statusamong other things“, the company announced.
“Storm-0539 operations are persuasive due to the perpetrators’ use of compromised legitimate emails and imitation of legitimate platforms used by the target company.”
Deception and the cloud
The development comes as Enea revealed details of criminal campaigns exploiting cloud storage services such as Amazon S3, Google Cloud Storage, Backblaze B2 and IBM Cloud Object Storage for SMS-based gift card scams that redirect users to malicious websites with l aim of stealing sensitive information.
“The URL linking to the cloud storage is distributed via text messages, which appear authentic and can therefore bypass firewall restrictions“, said the researcher by Enea Manoj Kumar.

“When mobile users click on these links, which contain domains of well-known cloud platforms, they are directed to the static website stored in the storage bucket. This website then automatically forwards or redirects users to embedded spam URLs or dynamically generated URLs using JavaScript, all without the user being aware.”
In early April 2023, Enea also discovered campaigns involving URLs constructed using Google’s legitimate address, “google.com/amp,” which is then combined with encoded characters to hide the scam URL (the famous misleading links, which you should never click on).
“This type of trust is exploited by bad actors who try to deceive mobile subscribers by hiding behind seemingly legitimate URLs,” Kumar pointed out. “Attackers’ techniques may include luring subscribers to their websites under false pretenses, and the theft of sensitive information such as credit card details, email or social media credentials, and other personal data.”
#Fraudulent #gift #cards #100k #stolen #Moroccan #group
