The China-linked advanced persistent threat (APT) group, codenamed APT41, is suspected to use an “advanced and updated version” of a malware known as StealthVector to spread a previously undocumented backdoorcalled MoonWalk.
It is worth noting that the Chinese hacker group APT41 is already known as it has used other more or less known malware in the past, one of which was GC2, a type of attack that was delivered via phishing emails.
Software updates APT41 has made to its malware
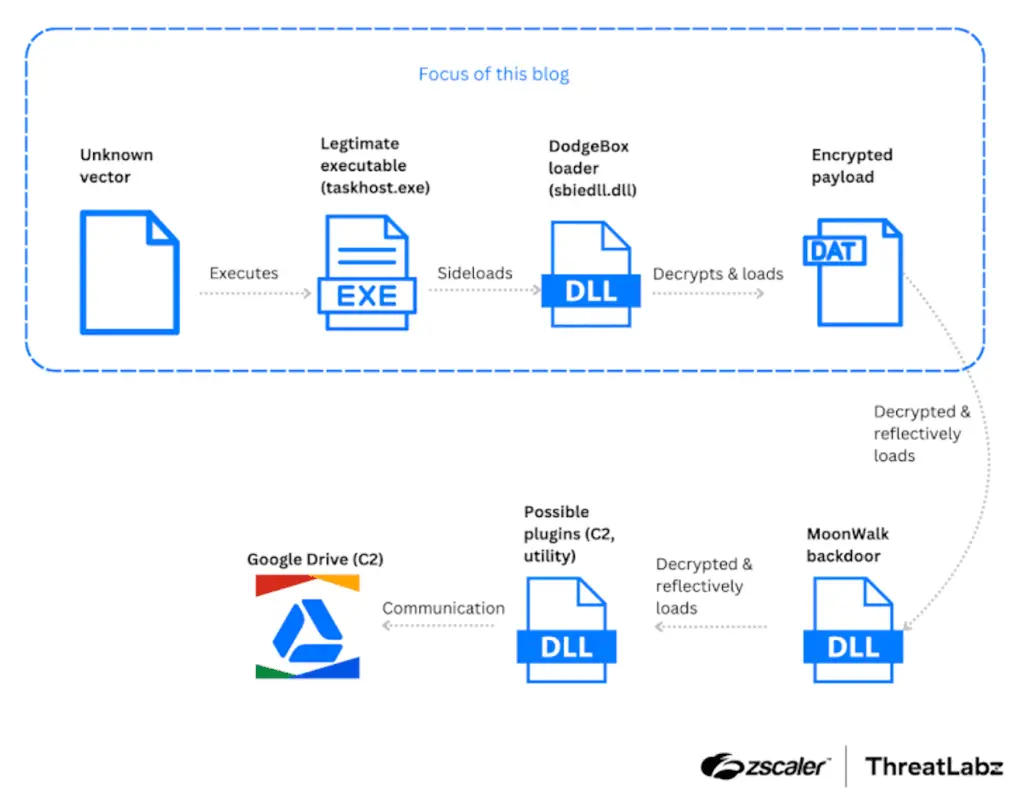
The new variant of StealthVector, which is also called DUSTPAN, has been designated DodgeBox by Zscaler ThreatLabz, who discovered the loader in April 2024.
“DodgeBox is a loader that proceeds to load a new backdoor called MoonWalk“, they have said security researchers Yin Hong Chang and Sudeep Singh. “MoonWalk shares many evasion techniques implemented in DodgeBox and uses Google Drive for command and control (C2) communication.“
APT41 is the name given to a prolific cybercriminal group that is linked and affiliated with China, and is known to have been active since at least 2007; is also followed by the cybersecurity community under the names Axiom, Blackfly, Brass Typhoon (formerly Barium), Bronze Atlas, Earth Baku, HOODOO, Red Kelpie, TA415, Wicked Panda, and Winnti.
APT41: A Threat from the Not-So-Distant Past
In September 2020, the U.S. Department of Justice (DoJ) announced the indictment of several cybercriminals who were associated with the Chinese hacking group for orchestrating intrusion campaigns that targeted more than 100 companies worldwide.
“The intrusions […] facilitated the theft of source code, software code signing certificates, customer account data, and valuable corporate information“, has said the DoJ at the time, adding that they also enabled “other criminal schemes, including ransomware and crypto-jacking schemes‘.”
In recent years, the threat group has been connected to breaches of U.S. government networks between May 2021 and February 2022, as well as attacks which targeted Taiwanese media organizations using an open-source red teaming tool known as Google Command and Control (GC2), as previously mentioned.
Malicious .DLL Files and Where to Find Them…
APT41’s use of StealthVector was documented first reported by Trend Micro in August 2021, describing it as a shellcode loader written in C/C++ used to distribute Cobalt Strike Beacon and a shellcode implant called Scramble Cross (also known as Sidewalk).
DodgeBox is rated as an improved version of StealthVector, which also incorporates various techniques such as call stack camouflage, DLL side-loading and DLL hollowing to evade detection, However, the exact method by which the malware is distributed is currently unknown..
“APT41 uses DLL side-loading as a means to run DodgeBox“, the researchers said. “They use a legitimate executable (taskhost.exe), signed by Sandboxie, to load a malicious DLL (sbiedll.dll).“
Potential harm of “rogue” .DLL files
The malicious DLL file (i.e. DodgeBox) is a DLL loader written in C that acts as a conduit to decrypt and launch a second-stage payload, the MoonWalk backdoor.
The attribution of DodgeBox to APT41 stems from the similarities between DodgeBox and StealthVector; the use of DLL side-loading, a technique widely used by China-linked groups to distribute malware like PlugX; and the fact that DodgeBox samples were submitted to VirusTotal from Thailand and Taiwan.
“DodgeBox is a recently identified malware loader that uses multiple techniques to evade both static and behavioral detection“, said the researchers who concluded by adding that “It offers various capabilities, including decrypting and loading embedded DLLs, conducting environmental checks and bindings, and performing cleanup procedures.“
#APT41 #Chinese #hacker #group #strengthens #arsenal