A previously unknown malware, called SambaSpy, is taking aim exclusively users in Italy through a phishing campaign orchestrated by a suspected Brazilian Portuguese-speaking cybercriminal.
SambaSpy, here’s how it works
“Cybercriminals usually try to target a large number of victims to maximize their profits, but these attackers focus on just one country.“, has declared Kaspersky in a new analysis. “It is likely that the attackers are testing on Italian users before expanding the operation to other countries..”
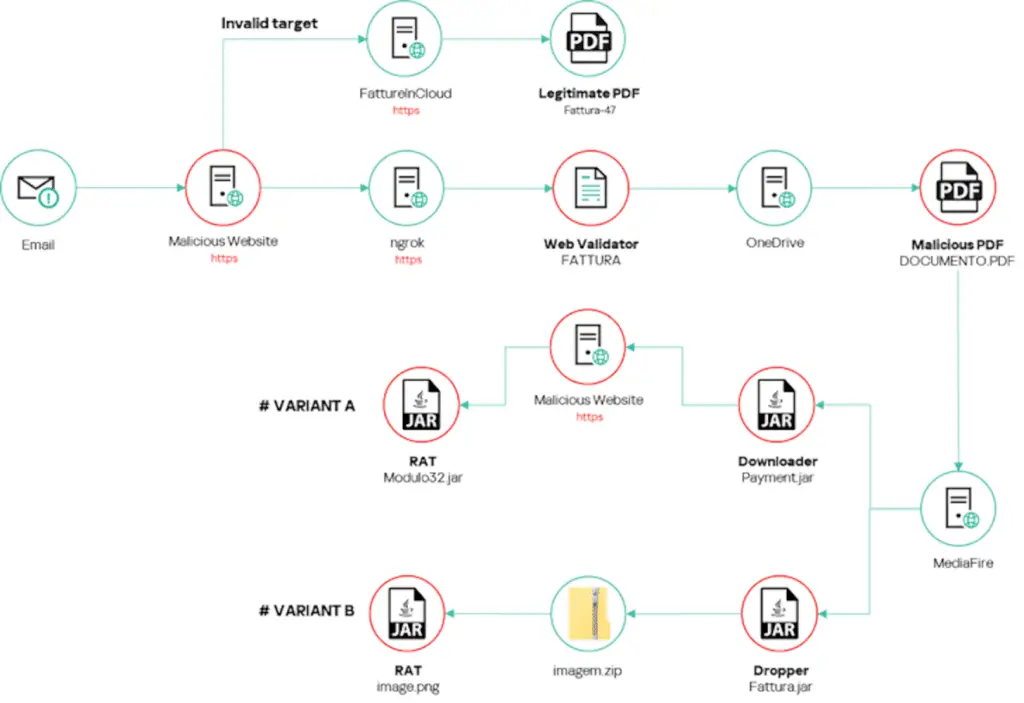
The starting point of the SambaSpy attack is a phishing email that includes an HTML attachment or an embedded link that starts the infection process. If the HTML attachment is opened, a ZIP archive containing an intermediate downloader or dropper is used to distribute and launch the payload of the multifunctional RAT (Remote Access Trojan).
The SambaSpy downloader, on the other hand, is responsible for retrieving the malware from a remote server. The dropper, on the other hand, does the same but extracts the payload from the archive instead of retrieving it from an external location.
The second infection chain with the trap link is much more elaborate, as clicking on it redirects the user to a legitimate invoice hosted on FattureInCloud, if it is not the intended target.
SambaSpy also has a sort of “plan B”
In an alternative scenario, clicking on the same URL takes the victim to a malicious web server that serves an HTML page with JavaScript code containing comments written in Brazilian Portuguese.
“Redirects users to a malicious OneDrive URL only if they are using Edge, Firefox, or Chrome with the language set to Italian“, the Russian cybersecurity vendor said. “If users fail these checks, they remain on the page..”
Users who meet these requirements receive a PDF document hosted on Microsoft OneDrive that instructs them to click a link to view the document, after which they are directed to a malicious JAR file hosted on MediaFire, containing the downloader or dropper, as before.
SambaSpy, a remote access trojan completely developed in Java, is a sort of Swiss army knife, capable of managing the file system, processes, remote desktop, file upload/download, Webcam control, keystroke and clipboard recording, screenshot capture, and remote shell access.
SambaSpy can load additional plugins on browsers
It also has the ability to load additional plugins in real time by launching a file on the disk previously downloaded by the RAT, allowing it to increase its functionality as needed. Furthermore, it is designed to steal credentials from web browsers such as Chrome, Edge, Opera, Brave, Iridium and Vivaldi.
Infrastructure evidence suggests that the cybercriminal behind the campaign is also targeting Brazil and Spain, indicating operational expansion.
“There are various connections to Brazil, such as linguistic artifacts in the code and domains that target Brazilian users.,” Kaspersky said. “This is in line with the fact that Latin American attackers often target European countries with closely related languages, namely Italy, Spain and Portugal..”
Beyond SambaSpy: New BBTok and Mekotio Campaigns Target Latin America
SambaSpy isn’t the only problem. The development comes just weeks after Trend Micro warned of a rise in campaigns distributing banking trojans such as BBTok, Grandoreiro And Mekotio, targeted the Latin American region through phishing scams that use corporate transactions and justice-related transactions as bait.
Mekotio “employs a new technique where the Trojan’s PowerShell script is now obfuscated, improving its ability to evade detection“, has declared the company, highlighting BBTok’s use of phishing links to download ZIP or ISO files containing LNK files that act as a trigger point for infections.
The LNK file is used to advance to the next step by launching the legitimate MSBuild.exe binary, which is present inside the ISO file and subsequently loads a malicious XML file also hidden inside the ISO archive, which then uses rundll32.exe to launch the BBTok DLL payload.
“By using the legitimate Windows utility MSBuild.exe, attackers can execute their malicious code while evading detection.“, Trend Micro noted.
Attack chains associated with Mekotio start with a malicious URL in the phishing email that, when clicked, directs the user to a fake website that delivers a ZIP archive, containing a batch file designed to run a PowerShell script.
The PowerShell script acts as a second-stage downloader to launch the Trojan through an AutoHotKey script, but only after performing a reconnaissance of the victim’s environment to confirm that they are indeed located in one of the targeted countries.
“More sophisticated phishing scams targeting users in Latin America to steal sensitive banking credentials and conduct unauthorized banking transactions underline the urgency of improved cybersecurity measures against increasingly advanced methods employed by cybercriminals,” Trend Micro researchers said, concluding: “These Trojans have become increasingly adept at evading detection and stealing sensitive information, as the criminal gangs behind them become bolder in targeting larger groups for greater profits.“
#SambaSpy #Brazilian #Malware #Targets #Italian #Users