The cryptocurrency hacking group, known as Kinsing, has established the ability to continuously evolve and adapt, proving itself to be a persistent threat by quickly integrating recently disclosed vulnerabilities into its arsenal of exploits to expand its botnet.
The discoveries come from cloud security company Aqua, which described the hacker group as having been active in orchestrating illicit cryptocurrency mining campaigns since 2019.
What does the Kinsing group aim for?
Kinsing (also known as H2Miner), a name given to both the malware and the adversary behind it, has steadily expanded its toolkit with new exploits to enlist infected systems into a cryptocurrency mining botnet; was first documented by TrustedSec in January 2020.
In recent years, campaigns involving Golang-based malware have weaponized various flaws in Apache ActiveMQApache Log4j, Apache NiFi, Atlassian ConfluenceCitrix, Liferay Portal, Linux, Openfire, Oracle WebLogic Server And SaltStack to breach vulnerable systems.
Other methods have also involved exploiting poorly configured Docker, PostgreSQL and Redis instances to gain initial access, after which terminals are routed into a cryptocurrency mining botnet, but not before disabling security services and removing rival miners already installed on the hosts.
The analyzes of computer security researchers
A subsequent analysis by CyberArk in 2021 revealed similarities between Kinsing and another malware called NSPPS, concluding that both strains “represent the same family.”
Kinsing’s attack infrastructure is divided into three main categories: seed servers used for scanning and exploiting vulnerabilities, download servers responsible for staging payloads and scripts, and command and control (C2) servers that maintain contact with the compromised servers.
The IP addresses used for C2 servers resolve to Russia, while those used to download scripts and binaries extend to countries such as Luxembourg, Russia, the Netherlands, and Ukraine.
“Kinsing targets various operating systems with different tools“Aqua said. “For example, Kinsing often uses shell and Bash scripts to exploit Linux servers.“
“We’ve also seen Kinsing target Openfire on Windows servers using a PowerShell script. When running on Unix, it usually tries to download a binary that runs on x86 or ARM.”
Another notable aspect of the campaigns of this cybercriminal group is that 91% of the targeted applications are open-source, with the group primarily targeting runtime applications (67%), databases (9%), and cloud infrastructure (8%).
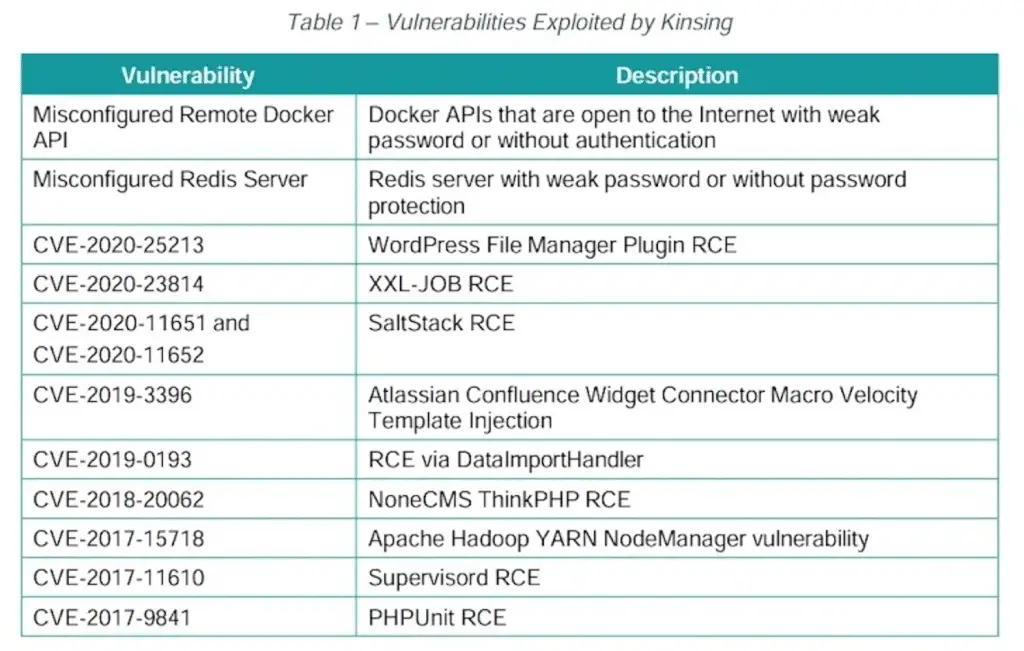
An in-depth analysis of the artifacts further revealed three distinct categories of programs:
- Type I and Type II scriptswhich are distributed after initial login and are used to download later-stage attack components, eliminate concurrency, evade defenses by disabling the firewall, terminate security tools such as SELinux, AppArmor, and Aliyun Aegis, and deploy a rootkit to hide malicious processes
- Auxiliary scriptsdesigned to gain initial access by exploiting a vulnerability, disable specific security components associated with Alibaba and Tencent cloud services from a Linux system, open a reverse shell to a server under the attacker’s control, and facilitate recovery of miner payloads
- Binarieswhich act as second-stage payloads, including the Kinsing core malware and the crypto-miner to undermine Monero
How this hacker group’s malware works
The malware, for its part, is designed to track the mining process and share its process identifier (PID) with the C2 server, perform connectivity checks and send execution results, among other things.

“Kinsing targets Linux and Windows systems, often exploiting vulnerabilities in web applications or misconfigurations such as the Docker API and Kubernetes to run cryptominers“Aqua said. “To prevent potential threats like Kinsing, proactive measures like hardening workloads before deployment are crucial.“
The disclosure comes as botnet malware families are finding ever-newer ways to expand their reach and recruit machines into a network to carry out malicious activity.
Learn more about the malware released by Kinsing
This is best exemplified by P2PInfect, a Rust malware that was found exploiting poorly secure Redis servers to distribute variants compiled for MIPS and ARM architectures.
“The main payload is capable of performing various operations, including propagation and distribution of other modules with file names that speak for themselves such as miner and winminer“said Nozomi Networks, which discovered samples targeting ARM earlier this year.
“As the name suggests, the malware is capable of performing Peer-to-Peer (P2P) communications without relying on a single Command and Control (C&C) server to propagate attacker commands.”
#Kinsing #hacker #group #hijacks #money #cryptocurrencies