Some unidentified cyber criminals they are exploiting fake job adverts on Facebook as bait to deceive potential victims in the installation of a new Windows-based stealer malware, called Ov3r_Stealer.
How the Ov3r_Stealer malware works
“This malware is designed to steal credentials and wallets [Wallet] cryptographic and send them to a Telegram channel that the cybercriminal monitors“, has declared Trustwave SpiderLabs in a report written by the company.
Ov3r_Stealer is capable of stealing information based on IP address, hardware information, passwords, cookies, credit card informationauto-builds, browser extensions, crypto wallets, Microsoft Office documents, and a list of antivirus products installed on the compromised host.
While the exact goal of the campaign is unknown, the stolen information is likely to be offered for sale to other cyber criminals; however another hypothesis is that Ov3r_Stealer may be updated over time to act as a loader similar to QakBot for additional payloads, including ransomware.
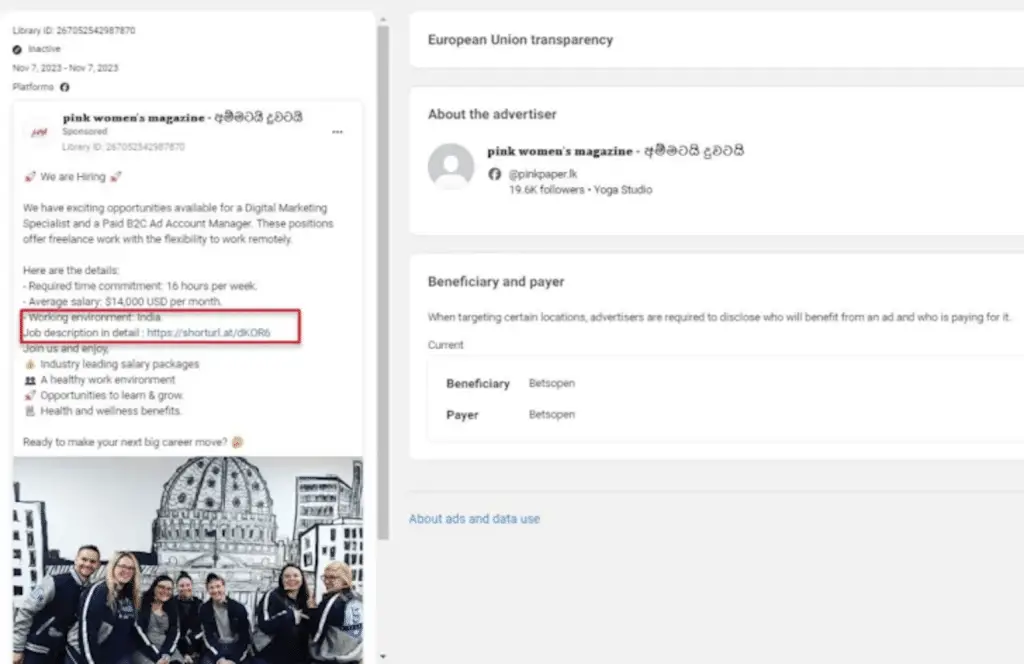
The starting point of the attack is a weaponized PDF file that purports to be a file hosted on OneDriveencouraging users to click on an “Document Access” button embedded in it.
Trustwave said it identified the PDF file shared on a fake Facebook account impersonating Amazon CEO Andy Jassy, as well as through digital advertising job ads on Facebook.
Users who click on the button are served with an internet link file (.URL) which masquerades as a DocuSign document hosted on the distribution network of Discord content (CDN). The link file then acts as a conduit to deliver a Control Panel Item (.CPL) file, which is then executed using the Windows Control Panel binary process (“control.exe“).
Running the CPL file leads to retrieval of a PowerShell loader (“DATA1.txt”) from a GitHub repository to finally launch Ov3r_Stealer.
It is worth noting that at this stage a almost identical infection chain was recently disclosed by Trend Micro as used by various cyber criminals to release another stealer called Phemedrone Stealer by exploiting Microsoft Windows Defender SmartScreen bypass vulnerability (CVE-2023-36025CVSS score: 8.8) e the similarities extend to the GitHub repository used (nateeintanan2527) and the fact that Ov3r_Stealer shares code-level overlaps with Phemedrone.
“This malware has been reported recently, and it may be that Phemedrone has been repurposed and renamed Ov3r_Stealer“said Trustwave. “The main difference between the two is that Phemedrone is written in C#.”

These findings come as Hudson Rock reveals that cybercriminals are advertising access to law enforcement request portals of important organizations such as Binance, Google, Meta and TikTok exploiting credentials obtained from infostealer infections.
They also follow the emergence of a category of infections called CrackedCantil which exploits cracked software as an initial access vector to release loaders such as PrivateLoader and SmokeLoader, which subsequently act as a kind of distribution mechanisms for information thieves, crypto miners, proxy botnets and ransomware.
Conclusion
In conclusion, the spread of the Ov3r_Stealer malware through fake job advertisements on Facebook highlights the continued creativity and danger of cyber criminals in the increasingly connected and the sophisticated infection chain, which exploits PDF files and internet links, highlights the need for greater awareness and attention on the part of
users when interacting with online content.
The possibility that stolen information will be offered on the market or that malware may evolve in the future raises further digital security concerns and it is therefore critical to keep cyber defenses up-to-date and adopt secure practices to mitigate the increasingly sophisticated threats emerging in today's digital landscape.
#Ov3r_Stealer #Malware #Fake #Job #Ads #Facebook